Version: Firmware 2024.2 K26MIPSR2_RTAC USB AIO-64K
Router Model: ASUS RT-AC66U
Overview
Testing out custom firmware in ASUS router above using build-in NGINX web server on custom http port. Trying to figure out how this custom firmware can blocks incoming hacker by their IP.
Web server log is able to log visitors' IP, and the URL request URI. So I can figure out the attackers' IP, which I considered as hacker.
This gives me an idea how aggressive hacker community and search engine will send valid and invalid attacks to a random web site.
I am leveraging build-in software firewall which configures using command iptables, configuration file /etc/iptables, web GUI called "Access Restriction" that stores in NVRAM (access using command "nvram get rrule0" and "nvram set rrule0"). Research of iptables chains and rules found that the menu "Access Restriction" is only restrict WAN to LAN, and doesn't restrict build-in NGINX web server, which is not consider in the LAN subnet. So this post document how to configure it to leverage "Access Restriction."
Initially, I uses following methods to configures the software firewall to block hackers' IP, but it is not persistent:
1. /etc/iptables configuration file, with scheduler
2. Using iptables command, with scheduler
Every few hours, Fresh Tomato seems to replace the above 2 files and configuration with the value in web GUI, which later found the setting is stored in NVRAM. So I lost all my firewall setting, and hacker can attack my NGINX web server again. It took me few days to figure out the web GUI menu called "Access Restriction" will configures iptables, and its setting is permanently stores in NVRAM in addition of above 2 files/configuration, even after reboot or power cycle.
Google search is not returning any info about blocking hacking using Fresh Tomato on build-in NGINX web server, but finally I found following Fresh Tomato documentation that gives me a clue how to configure NVRAM (so that I can blocked hacker by using NGINX access.log file):
- https://wiki.freshtomato.org/doku.php/access_restrictions
Web GUI's "Access Restriction" configuration resides in NVRAM, and needs to set using "nvram set [internal rule name]" command. Its current configuration can be retrieve using command "nvram get [internal rule name]" command. The internal rule name starts with rrule0, follows by rrule1, rrule2, and each can be enabled and disabled separately. Moreover, you can set the time start/end for every day, and the router will automatically trigger iptables command by the schedule.
In this post, I will assume there is no rule set, so I will use rrule0. This indirectly will create iptables chain name "rdev00."
Every time the "Access Restriction" configuration is changed, it will reload the configurations from NVRAM, as well as certain network related configurations in the router. I need to adds custom iptables command into "Scripts" section called "Firewall" as well to modify OOTB iptables chain to apply "Access Restriction" configuration in addition of LAN traffic.
Procedure
1. Creates rule #1 with:
1.1. Rule name: Blocks Hacker 2024-07
1.2. Blocks IP: 103.246.195.85, 5.183.103.248, 118.123.105.93
2. Connects to the LAN port using cable, or WiFi
3. Assumes WiFi router's IP is 192.168.100.1, then uses ssh utility such as PuTTY to ssh to port 192.168.100.1
4. Login as root user
5. At the "#" shell prompt, creates a new rule 1 with internal rule name rrule0
5.1. nvram set rrule0="1|-1|-1|127|104.37.174.65>117.146.152.81>118.123.105.93|||0|Blocks Hacker 2024-07"
5.2. Expect output:
root@rt-ac66u:~# nvram set rrule0="1|-1|-1|127|104.37.174.65>117.146.152.81>118.123.105.93|||0|Blocks Hacker 2024-07"
root@rt-ac66u:~#
6. Login to WiFi routner's web GUI to check. URL: http://192.168.100.1
7. On left menu, lick on menu item "Access Restriction" to display all the rules
8. You will see the first rule call "Blocks Hacker 2024-07" on the right panel, and as the 1st rule in the list
9. Following is the expected output
10.1. Only in configuration of NVRAM, but not saved yet
10.2. Current setting will lost after reboot, or power lost
10.3. Router has not run iptables to activate the setting. There is delay of about 1 hr
11. To make this setting permanent after reboot, enter: # nvram commit
12. Waits for about 1 hr, and checks firewall to see the IP are blacklisted. Command: iptables -L rdev00 -n
13. Expected output:
Chain rdev00 (1 references)
target prot opt source destination
DROP all -- 104.37.174.65 0.0.0.0/0
DROP all -- 117.146.152.81 0.0.0.0/0
DROP all -- 118.123.105.93 0.0.0.0/0
14. If you want to force the setting to activate immediately, runs these 2 commands:
# nvram set action_service=restrict-restart
# kill -USR1 1
# kill -USR1 1
15. You will see following in /var/log/messages:
# tail /var/log/messages | grep "Activating rule"
Jul 14 11:23:31 rt-ac66u user.info rcheck[1867]: Activating rule 0
16. Lastly, modify iptables firewall's INPUT chain to make web server port from the web GUI
16.1. In router's web GUI, on left panel, navigates to Administration > Scripts
16.2. Click on tab Firewall
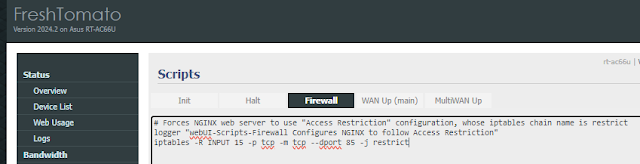
16.3. Enter following command to create a new custom chained called "hacker" and replaces exiting rule for NGINX TCP port 85 to this custom chain:
logger "webUI-Scripts-Firewall Configures NGINX to follow Access Restriction"
iptables -N hacker
iptables -A hacker -j restrict
iptables -A hacker -j logaccept || iptables -A hacker -j ACCEPT
iptables -R INPUT 15 -p tcp -m tcp --dport 85 -j hacker
16.4. Sample screenshot
Maintenance
You might to perform other maintenance of the firewall.
1. Removes/delete the rule, e.g. removes rule 10: nvram unset rrule10
2. Delete firewall rule 10 (rdev09):
2.1. iptables -D restrict -j rdev09
2.2 .iptables --flush rdev09
2.3. iptables -X rdev09
3. Checks current actively blocked IP for rule 1 (chain name rdev00) in memory: iptables -L rdev00 -n
4. Checks current block IP for rule 1 in /etc/iptables configuration file: grep rdev00 /etc/iptables
5. Forces Access Restriction to activate now:
5.1. Command #1: nvram set action_service=restrict-restart
5.2. Command #2: kill -USR1 1 (after above completed)5.3. Command #3: nvram get action_service (if completed, command will not return any value. If not completed, then returns "restricgt-restart")
6. Uses "top" Linux command to monitor the CPU usage with the new firewall rule. You will need to reduces number of blocked IP, if encountered CPU contention, or buy a faster/newer WiFi router
Known Limitation
Web GUI's menu Administration > Logging > Syslog > Connection Logging to control following won't always going to capture above traffic:Inbound: If blocked by FirewallOutbound: If blocked by FirewallReason: above logic/commands need to modify to use iptables chain "logaccept" and "logdrop" which will make it longer to write(updated to allows logging to syslog /var/log/messages)- iptables firewall configuration is based on my configuration of Fresh Tomato on ASUS RT-AC66U, version 2024.2. It might needs further modification
- When number of blocked IP is getting long (more than 100), the web GUI's menu "Access Restriction" won't be able to delete or modify rule #1, and will consistently prompt to delete IPs (then it will work)
- Fresh Tomato firmware seems to enforce a restriction to limit the number of entries inside the rule
- This error can be ignore, and doesn't affect the IP blocking


1 comment:
I’ve been using Fresh Tomato with Mumble 1.3.3 and honestly, the combo is rock-solid. No more random pings or weird lag just smooth, secure performance. Totally worth setting up!
Post a Comment